Available for Enterprise customers.
How Secrets Are Protected
1. Encrypted in Transit
The secret is encrypted during transit to our server by HTTPS to avoid man-in-the-middle attacks.2. Encrypted at Rest
Our server stores secrets using Google Cloud Platform (GCP) Secret Manager, where they are encrypted at rest.3. Minimal Memory Exposure
When the Custom AI Navigation agent follows its execution script:- It accesses the secret and loads it into memory
- Uses it for the required action (e.g., filling a password field)
- Immediately deletes it from memory
Secrets are never sent to any LLM. The secret is only accessed by our server momentarily while being sent to the browser.
Security Architecture
The storage and usage of secrets is similar to a password manager: everything is encrypted until the exact moment it’s needed, at which point it is accessed, used, and then immediately forgotten.
When to Use Secrets
Use the Secret data type for:- Login passwords
- API keys and tokens
- Authentication credentials
- Any sensitive value that should not be visible in logs or UI
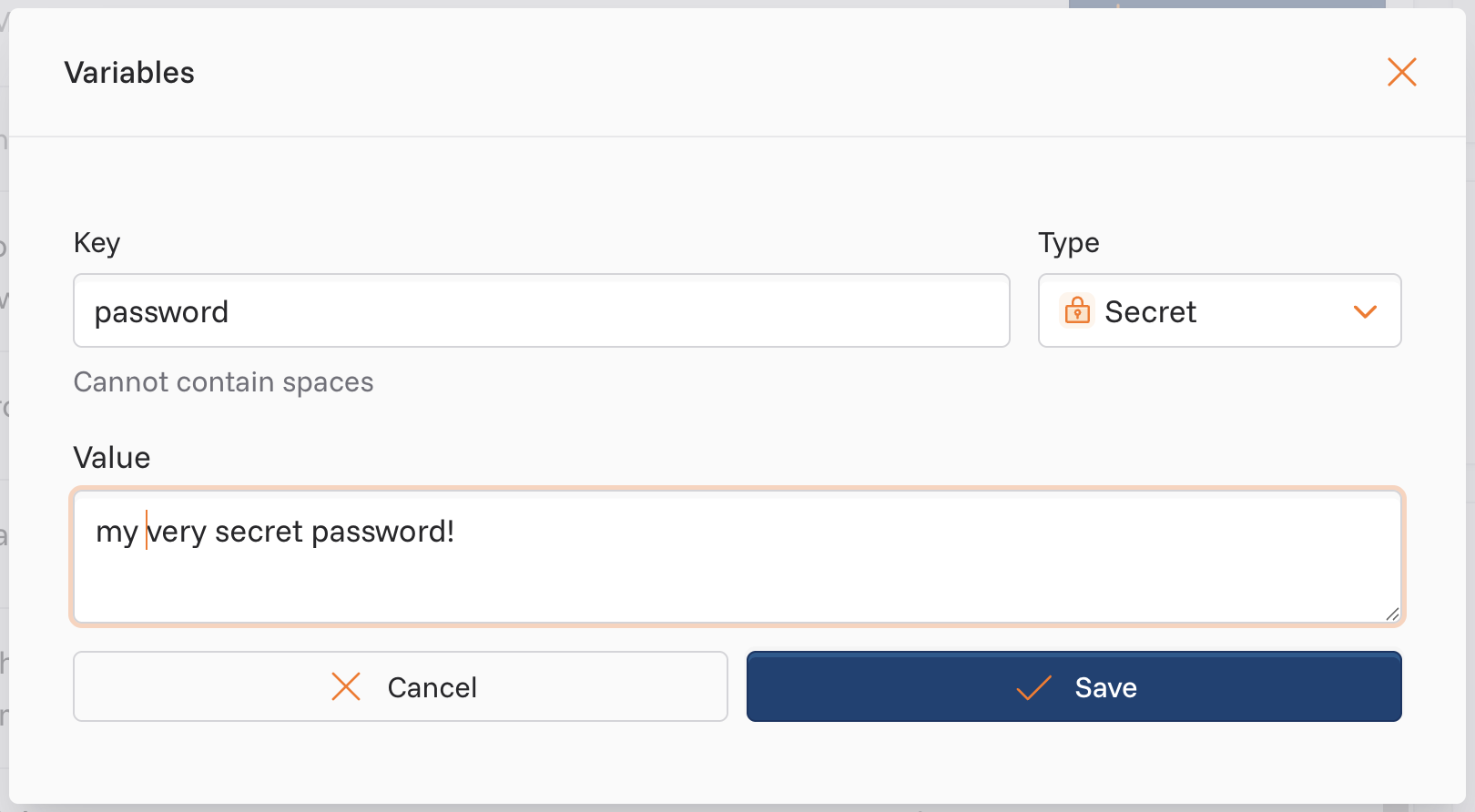
Creating a Secret Variable
- Navigate to Team Settings in your dashboard
- Click Add variable
- Enter a unique Key (e.g.,
portalPassword) - Select Secret as the Data Type
- Enter the secret value
- Click Save
••••••••) after saving. You cannot view it again.
Using Secrets in Prompts
Reference secrets the same way as regular variables:@password is a Secret variable.